Solving The Classic Problem Of The Best Media Player Audio Codec
December 8, 2021
Here are some simple methods that can help you fix the problem of the best classic media player with audio codec.
Recommended: Fortect
K-Lite was the most complete package of Media Player Classic codecs for installing all related codecs, but it remained a bit autocratic: once you figure out that you are installing K-Lite as an MPC codec, it will detect and remove – any other broken codecs or DirectShow filters on your Windows system.
But despite the fact that the Internet is an indispensable tool, it makes us vulnerable to malicious threats. There are many Trojans, bots, malware, ransomware, viruses, scammers, spyware, red wigglers, and phishing attacks targeting Internet users on a daily basis. Criminal software attacks and identity fraud can affect anyone at any time, and the more we use the Internet, the more vulnerable we become to threats.
The K-Lite Codec Pack is a collection of DirectShow filters, VFW / ACM codecs and tools. DirectShow codecs and filters are used to encode and decode audio and movie formats. The K-Lite Codec Pack is truly designed to be an easy-to-use solution for playing all your audio and video files.
There are many security measures that website visitors can take in order to be targeted for revenge attacks. If you are under attack, read the instructions you can take in response to the incident.
Criminal Software
If you are the victim of a malware attack, you should immediately disconnect from the Internet. If it is connected hVia Wi-Fi, phone or Ethernet cable, you should disconnect part of the connection as soon as possible to prevent transmission of data to some attackers. Loss of network connectivity is the best way to stop the attack immediately.
You can easily disable your internet connection by actually turning off your router or infrastructure connection and also disabling the attachment on your device by following these steps:
- Click the start menu.
- Click Settings.
- From the settings menu, select “Network and Connections”.
- Right-click to select the Disable option.
If an attack occurs during your work, contact your IT department immediately. Your company’s IT department must determine whether the contamination prevents the spread or compromise of your personal and boss information. Then your IT department can always take the right action to repair the damage caused. If someone’s personal device has been attacked, contact your current ISP.
It’s good practice – andNote installed and updated antivirus software, such as Norton ™ AntiVirus or Norton ™ Internet Security, in case of such an incident. Antivirus, anti-spyware and software are the best defense against criminal software. Run periodic diagnostic scan using the pair software; Run automatic scans regularly to better protect your device.
Know your enemy.Reduce the size of Internet Explorer.Discourage downloading.Teach the basics of backup and recovery.Createreal spyware removal CD.Actually run two spyware cleaners.Close the holes in the desktop dialog box.Working with DRM.
To detect malware emanating from your device that can go undetected, antivirus and antispyware programs can often remove threats as well.
In some cases, products can detect criminal software, but cannot rewind it.
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!

Files and folders are usually backed up on a regular basis. While the ultimate goal of criminal software is usually to steal information or data, there is definitely a high chance that files will be completely lost or destroyed during this recovery process. You can create backups using software for backup, hard disk or removable media, most of which are CD or DVD drives.
Remember what you are getting yourself into. Avoid suspicious appearances and signs on websites, and remember that if something looks awesome or is too good to be factual, it is.
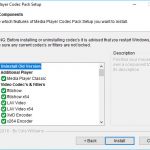
1. K-Lite codec pack. K-Lite Codec Pack – the most popular package of audio and video codecs for Windows 10/8 / 8.1 / 7 / Vista / XP, etc. popular video / audio files.
Depending on the severity of the attack, it may be necessary to reinstall the operating system on all of your computers; some threats are really complex and can use rootkit techniques to hide deep operations in the system, knowing that they come from them. Computer software goes unnoticed.
Norton software can restore your system to its last stable state prior to infection. In other cases, the date of infection may not be known and more important details may be compromised. In this case, the safest option is definitely to restore your operating system and reinstall the parts.
Int Online Fraud
Above 1. Media player codec pack. Windows only offers this package to users who can be used as an alternative to automatic software.for Windows Media codecs, as well as for any problems with previous codecs.Mountain peak. K-Lite Codec Pack.Top 3. Codec pack X.
When customers learn that you have been the victim of online fraud or identity theft, they should close all affected accounts first. If you work fast, you can close accounts before the thief can get into the business. Closing or suspending your account can certainly save you a lot of moments and stress later on when you have to dispute fraudulent purchases made by a cybercriminal. It’s always a good idea to contact a financial foundation and discuss the impact of the damage on your accounts, the amount, and what to do if your account has been hacked for a long time.
Set up fraud alerts at three national consumer registries: Equifax, Experian, and TransUnion. Contacting one of these companies will redirect the warning for all three. The Fraud Warning asks lenders to speak with you directly before making changes to existing accounts or allowing anyone (or anyone using your identity) to open new accounts. This is the oneIt is also an important step in combating further damage that a fraudster can cause by stealing your facts and strategies. This step also allows you to get free credit reports from almost any agency.
Keep an eye on your credit reports from any of these agencies, as I would say information in the reports might get some attention. It can take a few seconds for your reports to be scammed, which is why several agencies offer comprehensive reporting or timely notification services for an additional flat fee. In some cases, it may be particularly interesting to review one of these Rapid Processing reports, depending on the threat level and potential future impact.
Advertising. K-Lite Codec Pack Full is one of the most complete collections of codecs and related tools. It contains the latest codecs for playing and editing videos of the most popular sizes on the Internet. And although most people do not have a real media enthusiast, including business (Media Player Classic, Bsplayer, etc.).
Special vigilance should be exercised following an incident. D. flight. Pay attention to what is being mailed, for example: Check your credit card and incidental bills carefully every month. Ideally, you should also make sure that you can find all drinks and other prices to be shipped home to you. In some In other cases, you will most likely be contacted by sellers about bank accounts you have not yet opened, or debt lovers may contact you about purchases made by someone else.
Also, to protect yourself from online scams, do the following: * Create strong passwords with amounts and symbols and change them too often. * Avoid using unsecured public Wi-Fi CPA networks. * Don’t share too much on open media platforms.

Internet security threats are widespread and can cause significant damage if attacked. While our company has no control over cybercriminal activities, we can make the necessary decisions to protect ourselves and minimize the risk of being victimized by cybercrime by installing good online health and safety software, keeping our data safe and vigilant.
Download this software and fix your PC in minutes.When the activity is very unusual, the business is idle for only a day or two. In other special cases, this may take several months. Most businesses take a few to four weeks because they have a particular problem of not knowing what to do.
The fastest way to get rid of ransomware is to simply restore your existing systems from backups. For this secret to work, you must have the latest version of your data and applications, free of the ransomware that you are currently infected with. Before restoring, be sure to uninstall the ransomware first.
Two-thirds of expired companies believe it will take five or more days to thoroughly recover from a ransomware attack if they choose not to pay the full ransom, according to the 2020 Ransomware Resiliency Report, which was polled by 2,690 IT managers.
Miglior Lettore Multimediale Codec Audio Classico
Beste Audio Codec Mediaspeler Klassieker
Luchshij Audiokodek Mediapleer Klassicheskij
Meilleur Lecteur Multimedia De Codec Audio Classique
Mejor Reproductor Multimedia De Codec De Audio Clasico
최고의 오디오 코덱 미디어 플레이어 클래식
Melhor Codec De Audio Media Player Classico
Basta Audio Codec Mediaspelare Klassiker
Bester Audio Codec Media Player Classic
Najlepszy Klasyczny Odtwarzacz Multimedialny Z Kodekiem Audio