Fixed: How To Fix Windows Firewall Through Icmp Port.
December 20, 2021
This user guide will help you if you spot Windows firewall through the icmp port.
Recommended: Fortect
ICMP Firewall Rules (TCP / UDP Port 7)
On this page:
- Presentation
- Windows Firewall
- Third party firewall
Presentation
By default, Windows Advanced Security Firewall blocks ICMP echo requests from the network. You can of course take the plunge by disabling a specific firewall for testing purposes, but the simplest solution is to simply create an exception that allows ICMP requests through the firewall.
If someone has activated a firewall on Windows, Ping requests are blocked by default. This prevents University Information Security Office (UISO) vulnerability in functional scanners. To configure the software to allow pings, follow the instructions below.
Windows Firewall
- Search for
Windows Firewall, click to open it. - Left-click.
- Click in the left pane of the window that opens.
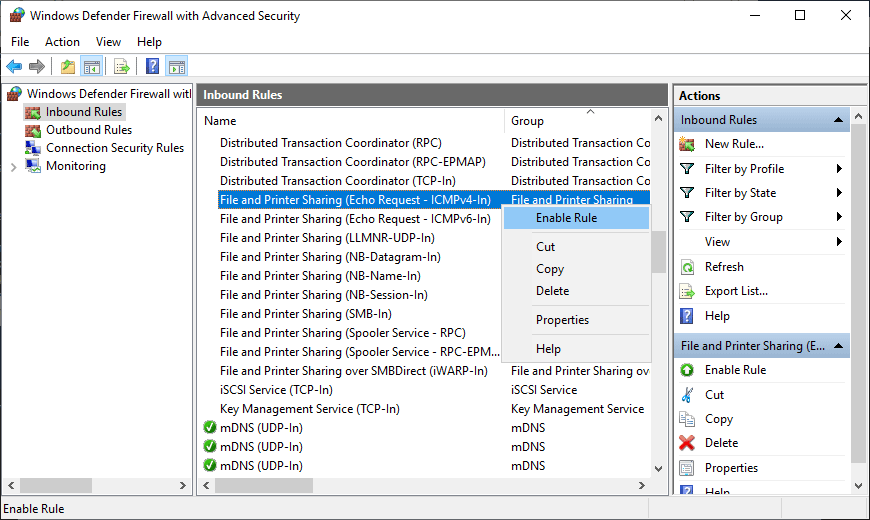
- In the right pane, find the rulers with the name.
- Right-click each rule and specify an option for.
Third Party Firewall
If you are using a third-party firewall or device, see Vulnerability Scanners.
Since every third-party firewall is considered to have a unique configuration, there is no way to help you cover all possibilities.Essential routes that will allow ping to be performed against all possible firewalls. However, you can use the following content to determine how to configure your firewall:
- Many firewalls can prevent blocking specific IP addresses and zones. UISO Scanner purchase IP ranges are specific to vulnerability scanners only.
- firewalls exclude certain protocols or websites. In these cases, you need to equip ping. Some firewalls define a “ping” or “ping in” call. Others call him by his Echo tech label “icmp Reply”. In any case, this protocol will allow.
- firewalls also provide options to allow specific ports for communication (do not confuse TCP network ports with only physical serial, parallel, USB, or Ethernet ports). Don’t worry about setting these configuration parameters for the UISO scanner; full “ping” (ICMP_Echo_Reply) must be enabled and no ports are used. You may want to allow or deny some vents for other reasons m, but this Scanner-Uiso is needed compactly.
Some
This is a copy of the knowledge base document.
Last modified on 02.12.2012 16:30:06.
On this page:
- Presentation
- Windows Firewall
- Third Party Firewall
Presentation
If you can turn on firewall on Windows, Ping requests are blocked by default. This prevents University Information Security Office (UISO) vulnerability in functional scanners. Follow these best practices to set up your plan to allow ping.
Windows Firewall
- Search for
Windows Firewalland click to open it. - Click on the left.
- Click on the left pane of our resulting window.
- Navigate to the rules listed in the right pane.
- Right-click each rule and select an option.
Third Party Firewallmanufacturer
If you decide to use third-party software or firewall devices, see Vulnerability Scanners.
Because every third-party firewall is uniquely configured, there is no guarantee that you will cover every ping test for every possible firewall. However, you can use the following information to determine how to configure your personal firewall:
- Many firewalls can prevent blocking specific IP addresses or zones. Displaying IP address ranges for UISO scanners by vulnerability scanners.
- firewalls exclude certain protocols or companies. In these cases, you will need to ping. Some firewalls refer to the locale as “ping” or “incoming ping”. Others call it the technical name Echo “icmp Reply”. Anyway, this protocol is available.
- firewalls also offer options to allow communication with specific ports (do not confuse TCP network ports with any physical serial, parallel, USB, or Ethernet ports). Not b Care about setting these parameters for the UISO scanner; The main “ping” (ICMP_Echo_Reply) must be enabled where it does not use ports. You can enable or disable some plugins for other reasons, but this is not necessary for the actual Uiso scanner.
Some
Many
- Presentation
- Windows Firewall
- Third Party Firewall
Presentation
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!

If you create an activated firewall on Windows, Ping requests are blocked by delay. This prevents University Information Security Office (UISO) vulnerability caused by working readers. To configure your firewall to allow ping requests, follow the instructions below.
Windows Firewall
- Search for
Windows Firewalland click to open it. - Click at the top left.
- Click on the left side of the destination window.
- In the right pane, find the rule type with a heading.
- Right-click each rule and select an option.
Third Party Firewall
Many infrastructure administrators believe that ICMP is a security risk and therefore need to make sure that a firewall is blocking it. It is true that ICMP currently has security problems and many ICMPs should be blocked. However, this is almost certainly not a reason to block all ICMP traffic!
If you use sideThis software or researching vulnerability scanners.
Since each third-party firewall is configured individually, it is impossible to cover every possible ping method, including every possible firewall. However, a person can use the following information to determine how to set up an actual firewall:
- Many firewalls can prevent blocking specific IP addresses or ovens. IP address ranges for UISO scanners can be found in the Vulnerability Scanners section.
- exclude certain protocols or services. In these cases, you need to enable callable ping. Some firewalls define the calling environment as “ping” or “ping in”. Others call it the technical name Echo “icmp Reply”. In any case, enable the above protocol.
- firewalls also offer options to guarantee ports for communication (don’t confuse the idea of TCP network ports with serial, parallel, USB, or Ethernet power ports). Don’t worry about setting these parameters for your scanner UISO; only “ping” (ICMP_Echo_Reply) must be enabled and it does not use any ports. You can allow or deny certain ports that are needed for other reasons, but you are not required to do this for Scanner-Uiso.
Some firewalls
Many
This is a copy of a document about basic human knowledge.
Last modified on 12/02/2021 16:30:06.
Firewall De Windows Del Puerto Icmp
Icmp Poort Windows Firewall
Zapora Systemu Windows Portu Icmp
Porta Icmp Firewall Do Windows
Pare Feu Windows Du Port Icmp
Icmp Port Brandmauer Windows
Icmp Port Windows Firewall
Icmp Port Windows Brandvagg
Icmp 포트 윈도우 방화벽
Icmp Port Windows Firewall