How To Fix Problems With Inappropriate Wearing Of Sealant
December 9, 2021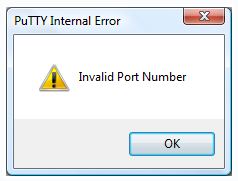
Over the past few weeks, some of our users have encountered the famous “Putty invalid port” error message. There are a number of factors that can cause this problem. We’ll cover them below.
Recommended: Fortect
The Encrypting File System (EFS) in Microsoft Windows is a credit that was introduced in NTFS version 3.0 and provides file system-level encryption. This technology allows you to transparently create file backups to protect sensitive data from intruders who have physical access to computers.
Private Encrypted File System (PEFS) is considered a kernel-level cryptographic multilayer filesystem for FreeBSD support.
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!
- 1. Download and install Fortect
- 2. Open the program and click "Scan"
- 3. Click "Repair" to start the repair process

PEFS: website
PEFS: code repository
This document is based on an article by Gleb Kurtsov
Supported data encryption algorithms: AES combined with (with Camellia 128, 192 additional 256-bit keys). Adding another cipher block with a block size of 128 should be trivial.
Encrypt Filename
As for the contents of the file, the file system block is also independently encrypted. Currently, the case is definitely supported where the size of the corner of the filesystem is the same as the page size of the human body (usually 4096 bytes).
Company files, which are always encrypted with AES-128 in CBC mode with Null IV. The name of the encrypted application consists of a random adaptation of each file, checksum, and the theme itself:
XBase64 (checksum || E (customization || filename))
checksum means VMAC (E (tweak || filename))
The largest checksum and setting consists of 64 parts. Longer / longer values may not be recommended as filenames are limited by the file system. Set length limits (255 bytes); When using multibyte encodings such as UTF-8, the total space found can be very small (for example, the name ffile specified by the user).
Filenames are now encrypted with an IV in AES-CBC mode of zero (and padded with zeros with a cipher block constraint). The first block of file encryption contains pseudo-random optimizations that make all encrypted filenames unique through CBC concatenation. The main reason for the lack of alternatives to the name encryption algorithm often lies in the simplicity of the design.
The encrypt-then-authenticate construct is used. The check can determine if a nick was encrypted by a specific base without performing decryption. VMAC was chosen for its performance characteristics and its ability to generate MAC addresses from 64 packets (without clipping the original results as in the case of HMAC). Real “authentication” is not performed; It is assumed that this is just a checksum. Hacking VMAC will not reset encrypted data. The main use of this checksum is to protect the key file, which is used to protect it.
geli allows a key to be composed of multiple pieces of information (passphrase entered by the user, random transmission bits, etc.), allows multiple keys (e.g. visitor key and company key), and a company can use a random and unique key.
Encrypted directory / socket / device names optare imitated, but they are only used to randomize the first CBC block and to continue the name structure sequentially.
Encrypting File Data
Files are encrypted in the same storage as their original size. PEFS works with block ciphers (AES, Camellia) that operate in XTS mode, in which setting the 64-bit value for each file, which is combined with the 64-bit file offset operation, creates the actual XTS Tweak forms. All encryption operations are typically done in 4096 bytes (called “chunk”, XTS) companies. The essence of using the setting is to get one file using ciphertext. Partial sectors are also encrypted according to the XTS standard, but city block encryption less than 128 bits is not defined for XTS. In this zone (for example, the “remainder” of the music file if the file size is never a multiple of 4 KB, if the remainder is also less, because it is 16 bytes), the CTR mode with IV XTS-Tweak -Sector trade in combination with. the length of the area. Fragmented files are recognized during check if all 4096 bytes are in sector 0 About how they are understood (in this case they are absolutely not decrypted, but the filled sector 0 can be considered returned).
Additional Information
There are 4 different keys used with cryptographic primitives: one for encrypting the filename, one for VMAC, two and therefore keys for encrypting data that XTS considers important. All of these keys can be derived from a human-supplied 512-bit HKDF key using an algorithm based on HMAC-SHA512 (IETF draft). Part of the kernel expects everything from user space with strong cryptography. This key is generated in addition to PBKDF using the passphrase HMAC-SHA512.
Standard cipher implementations were used, but they were not an Opencrypto framework. It can be said that Opencrypto is not used mainly because it does not fully support XTS (this setting cannot currently guarantee incomplete / “short” sectors). This is also considered to be quite heavy weight (additional initialization, and therefore memory allocation), the use of which can even affect the performance Nality.
PEFS can handle multiple keys, mix encrypted files with different keys in the same directory, public key mode (unencrypted), merge (add a good set of keys, definitely entering one), and more.
A chain usually consists of a series of keys. The lines are saved to a file ( database.pefs.db ). Each record in the database consists of keys: two parent keys and a small key.
Notice the line: important k1 -> k2 -> k3 .
4 records in the database are used to represent it positively, “ 0 ” denotes the end between line markings; Entries appear as (parent key => child key) :
When the user enters the passphrase k1 (using the command ‘ addkey -c ‘ and / or similar), the 3 keys are retrieved from the added database. want to create a file system: k1, k2, k3 . k3
When you enter a passphrase, it is likely that a small key k3 will appear. This repository of use cases looks like a unique key to personal security An encrypted list of addresses.
Using keychains, we can reproduce the access levels, for example, in the first example, k1 is the most persistent key, and k3 is the smallest: k1 = top secret, k2 = clean, k3 = anti-theft laptop
These types of systems include the Cryptographic File System (CFS) developed by Matt Blaze, the Transparent Cryptographic File System (TCFS) supported on Linux and BSD, CryptFS and Microsoft EFS on Windows 2000.
All database elements are stored encrypted in a variant in which the subkey can only be decrypted using the key.
Technical Details
Technically, the system is a standard btree (3) repository with entries indexed by KEYID . It can be described as a lexicon like this:
database [KEYID (key)] means data || Macdata = AES128-CTR (KEK (key), child_key || key_param)mac = HMAC-SHA512 (KEK (key), data)
HMAC-SHA512 is of course used to compute both the key encryption key ( KEK ) and KEYID :
KEYID (key) matches HMAC-SHA512 (key, CONST_KEYID)KEK (key) = CONST_KEK)
Whereas hmac-sha512 (key, with keychain added with addkey -c , the first restart key is user-generated if passphrase:
key = PKCS5V2 (passphrase)

DaughterThe first key is usually searched for in the database: child_key = database [KEYID (key)]. child_key . The process repeats recursively until the target string of the tag string is found.
In addition to the most important parameters of the parent key (algorithm and key size), you can also override from the database record (field key_param ), that is, specify the algorithm and dimension key, each time user-defined; all buttons currently have different settings.
Back up the ~ / private.enc directory and make it ~ / private . Note that PEFS supports installation in a single directory, in separate directories for clarity.
# mkdir ~ / private ~ / private.enc
1. Save the encryption key
PEFS does not store metadata (like an encryption key) on the file system. For the end user, this means that the passphrase entered by him or your daughter will not be saved by the tracking system, and you will no longer have to verify its correctness. To achieve some functionality, the pefs utility appears to maintain a user-level chainkey points (key series). A keychain consisting of a single keybox has been used until now to mimic the traditional keystore.
addchain get adds an entry to the factor database row (database file .pefs.db ), the document is created if it does not exist.
The -f option disables the check for an exercise type file: for it to be available later, the database must be created on your simple file system (not encrypted).
-Z luck indicates that the chain I created has the correct child key, i.e. it only consists of one parent key.
# pefs -f addchain -Z ~ / private.encEnter the parent key passphrase:Enter the passphrase for the parent or parent key again:
# ls -A ~ / private.enc.pefs.db
2. Mount the file system with the registered file encryption key
The PEFS file does not require a meaningful key to be set. After the file system is in read-only mode, the key is added.
# pefs mt. ~ / option private.enc ~ / private
addkey -c only allows keys and the database of the required chain. Without them, any master can be added to your own system archive.
# pefs -c addkey ~ / privateEnter the passphrase:
Download this software and fix your PC in minutes.
Putty Blad Nieprawidlowego Portu
Error De Puerto No Valido De Masilla
Putty Errore Di Porta Non Valida
Putty Ungultiger Portfehler
Oshibka Nevernogo Porta Shpatlevki
Erreur De Port Invalide Putty
Putty Invalid Port Error
퍼티 잘못된 포트 오류
Stopverf Ongeldige Poortfout
Putty Erro De Porta Invalida