How To Fix The Win32 Sohanad-Nak Worm?
August 19, 2021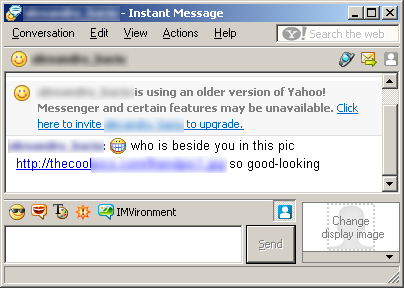
In this guide, we are going to find out some of the possible causes that the Sohanad-Nak Win32 worm can cause, and then I will suggest several ways for you to try to get rid of this problem.
Recommended: Fortect
After researching your current website for d watch, I found the following information:
Virus type: sohanad
Subtype: Ver
Detection date: 15.05.2007
Length: variable
Minimum DAT: 5031 (15.05.2007) Updated DAT: 5031 (15.05. 2007)
Minimum engine: 5.1.
Description with double zero Added: 05/15/2007
Description changed: 05/16/2007
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!

Overview -:
W32 / Hakaglan.worm has always been a worm written in AutoIT and spread through Messenger, Yahoo drives and network shares
Features -:
W32 / Hakaglan.worm is a worm written with AutoIT that streams Yahoo via Messenger, removable storage devices and network distributions
When launched, the worm deletes the following files:
% WINDIR% SSVICHOSST.exe -> worm component
% SYSDIR% SKCVHOSThk.dll -> keylogger component
% SYSDIR% SKCVHOST. exe -> keylogger component
% SYSDIR% SKCVHOSTr.exe -> keylogger component
Create the following registry keys that appear at system startup:
HKEY_LOCAL_MACHINE Software Microsoft Windows NT CurrentVersion Winlogon = “Shell” Explorer.exe SSVICHOSST.exe “HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
“Yahoo is equal to Messenger” “% SYSDIR% SSVICHOSST.exe”
The worm provides a task (At1 file.job) that returns to the schedule Every day at 9:00.
Modify the following registry clauses to change settings for hiding folders, disabling Task Manager, editing the registry, and more.
HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Policies Explorer
“NofolderOptions” = ” 1 “
HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Policies System
HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Policies System
” disabletaskmgr “=” DisableRegistryTools “=” 1 ”
HKEY_LOCAL_MACHINE SYSTEM CurrentControlSet Services Schedule
“AtTaskMaxHours” = â € 0â € – HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Explorer WorkgroupCrawler Shares
“shared” = ” [SHARES] New Folder.exe “
Symptoms -:
terminates the following types of procedures and exits applications if the header period:
[FireLion]
Bkav2006
System Configuration
Registry
Windows Task
cmd. exe
Download Component:
The worm connects to domains when you track it to download updated variants that are related to other malware.
At the time of this writing, various KeyLog-Perfect.dll, Keylog-Perfect, and Generic ProcKill.c have been downloaded. Like
Note. The submitted website should usually be controlled by the malware author, everything is loadednew binaries can be modified remotely, and the behavior of these new binaries can be changed, possibly every time a user is infected.
method when infected –
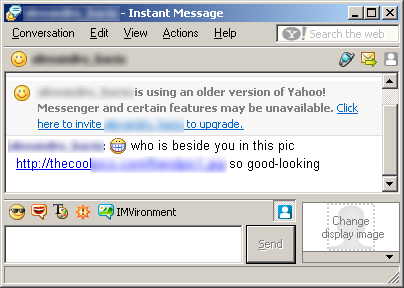
The worm spreads by forwarding one of the above affiliate links pointing to the hosted copy of the worm to all users posted in the crowd of infected Yahoo friends. Usually
Victims become infected when they can download and launch spam from the worm.
You can also use removable network shares and therefore drives.
Remove –
A combination of all the latest DAT files and the engine will be able to detect and eliminate this threat. AVERT recommends that users rely less on seemingly familiar or verified file characters, especially if they come from P2P clients, IRC, email, or other types of media on which media users can exchange data.
* Since we have many visits related to Hakaglan removal, we offer all possible assistance to help you remove this malware.
– W32 / Hakaglan.worm is a written worm in which autoit pdistributed via Yahoo Messenger, removable drives and network resources
– Alias: IM-Worm.Win32.Sohanad.t (Kaspersky) W32 .Yautoit (Symantec) W32 / Sohana-R (Sophos) Win32 / YahLover.AO (CA) Wurm / Sohanad.NAK (Avira)
– Method: Removing
1. Check your antivirus (who it is, whether it was updated, whether a full scan was performed on the PC (after the update).
2. If you cannot clean the worm with this method, reinstall the antivirus, download and install one of them from the AV site: McAfee or Kaspersky (here at SCForum.info, we provide you with a download link, check the correct section) and go even further from step 1.
3. Don’t forget to turn off System Restore on your computer.
4. Once again, the solution is to make this malware cleanup “handy”:
This malware interferes with the Registry Editor. To restore the said system tool altogether, follow the correct instructions:
Open Notepad, click Start> Run, type Notepad and press Enter.
Copy and paste the following:
In case of the following failover error
Install shl = CreateObject (“WScript.Shell”)
Install fso = CreateObject (“scripting.FileSystemObject”)
shl .RegDelete “HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Policies System DisableRegistryTools”
shl.RegDelete “HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion System DisableTaskMgr “
Save the file in the C: RESTORE.VBS folder.
Click Start> Run, type C: RESTORE.VBS, then press Enter.
Usually click Yes in the message box.
End Serious Malware
Open the Windows Task Manager program.
• Windows under 98 but ME,
CTRL + ALT + DEL
• Windows under NT, 2000, XP and Server ’03:
CTRL + SHIFT + ESC, then click the Processes tab …
In the list of running programs * find the process:
RVHOST.EXE
Select this malicious process and click the “End task” or “End process” button several times, depending on the version of Windows on your computer. …
To check if you should stop the malicious process, close Task Manager and reopen it.
Close the task manager.
———————————————– ——————————————– On
* Note : Computers running in a circle in Windows 98 and ME, Windows Task Manager cannot display certain types of processing. You can useUse a third eruption process viewer, such as Process Explorer, to stop the malware process.
On laptops that run on all Windows platforms, in cases where the process you see is not listed in Task Manager or Process Explorer, go to the next troubleshooting strategy and see additional instructions. If the process is usually on a list that can be read by Task Manager or Process Explorer, but you cannot end it, restart your computer in Safe Mode.
This malware personally modifies the registry. Users affected by certain malware may need to modify and delete certain registry keys or prices. For details on how to edit and improve the registry, see the following Microsoft articles:
HOW to: back up, edit and restore the registry for Windows 95, Windows 98 and Windows ME
HOW: back up, edit and restore the registry in Windows NT 4.0
HOW to go back Up: neg ddit and restore the registry in Windows 3000
HOW TO: Back up, modify and restore the registry in Windows XP as Server 2003
Remove the startup entry provided by the registry
Removing the autostart front panel from the registry prevents malware from running at startup.
If the registry entry below is frequently not saved, malware may not have been found. If you continue, move on to the next set of solutions.
Open Registry Editor.
Click Start> Run, type REGEDIT and press Enter.
In the Next to section, double-click the following:
HKEY_CURRENT_USER> Software> Microsoft> Windows> Current version> Run
In the right pane of the user, find and delete the entry:
Yahoo Messenger stands for “% System% RVHOST.exe “
(Note:% System% is the Windows policy folder, usually C: Windows System on Windows 98 and ME, C: WINNT System32 on Windows NT and 2000, and C: Windows System32 in Windows XP and Server 2003.) ->
Delete another registry entry
Still in the Registry Editor in the main left window, double-click the following:
HKEY_CURRENT_USER> Software> Microsoft> Windows> CurrentVersion> Policies> Explorer
Find or delete the entry in the right window:
NofolderOptions is “1”
restore modified registry entries
Still in the Registry Editor, in the left user pane, double-click the following: NT> CurrentVersion> Winlogon
hkey_local_machine> software> microsoft> windows
Select the right write area:
Shell = “Explorer.exe RVHOST .exe “
Right-click the value name and select Modify. Change the value range for this entry to:
Explorer.exe
Double-click the following in the window on the right:
HKEY_LOCAL_MACHINE> SYS
Download this software and fix your PC in minutes.
Win32 Sohanad Nak Worm
Win32 Sohanad Nak Wurm
Win32 Sohanad Nak Worm
Win32 Sohanad Nak Worm
Ver Win32 Sohanad Nak
Win32 소하나드 낙 웜
Worm Win32 Sohanad Nak
Win32 Sohanad Nak Cherv
Win32 Sohanad Nak Mask
Win32 Sohanad Nak Robak
Win32 Sohanad Nak Gusano
Win32 Sohanad Nak Wurm
Win32 Sohanad Nak Worm
Win32 Sohanad Nak Worm
Win32 소하나드 낙 웜
Ver Win32 Sohanad Nak
Worm Win32 Sohanad Nak
Win32 Sohanad Nak Mask
Win32 Sohanad Nak Cherv
Win32 Sohanad Nak Robak
Win32 Sohanad Nak Gusano