Troubleshooting And Fixing Kerberos Authentication Error 6863 Udp
November 26, 2021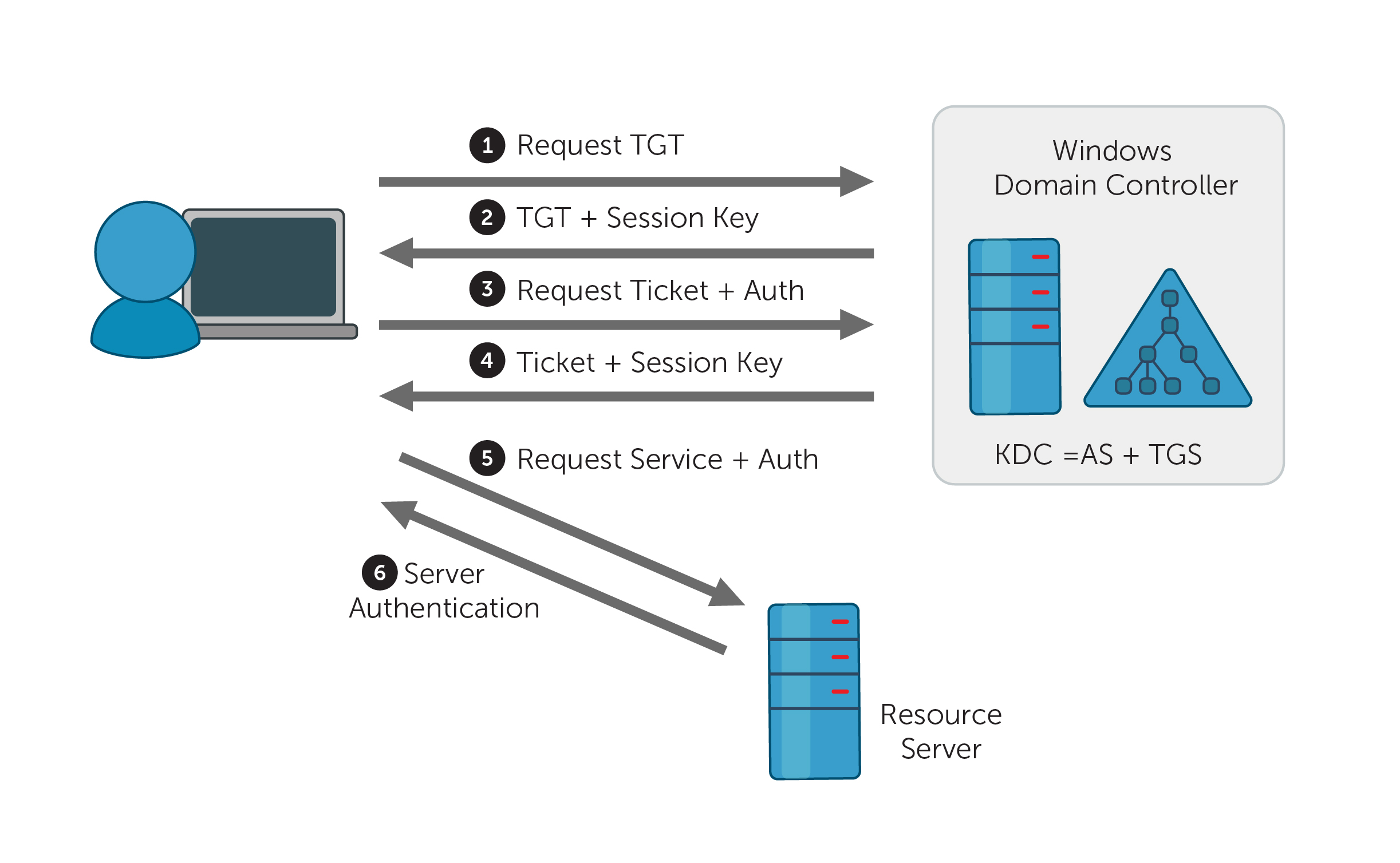
Recommended: Fortect
If you have Kerberos 6863 udp authentication error on your system, this article should help you fix the problem. Kerberos error codes are usually Kerberos result codes that indicate that something went wrong. Kerberos-related result code messages can appear on the KDC authentication server, on the installation server, in the user interface, or in Kerberos packet network traces.
This article describes how to try Kerberos to use TCP instead of referring to UDP.
Applies to: Windows 10 – all editions, Windows Server 2012 R2
Original Knowledge Base Number: 244474
Resume
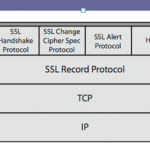
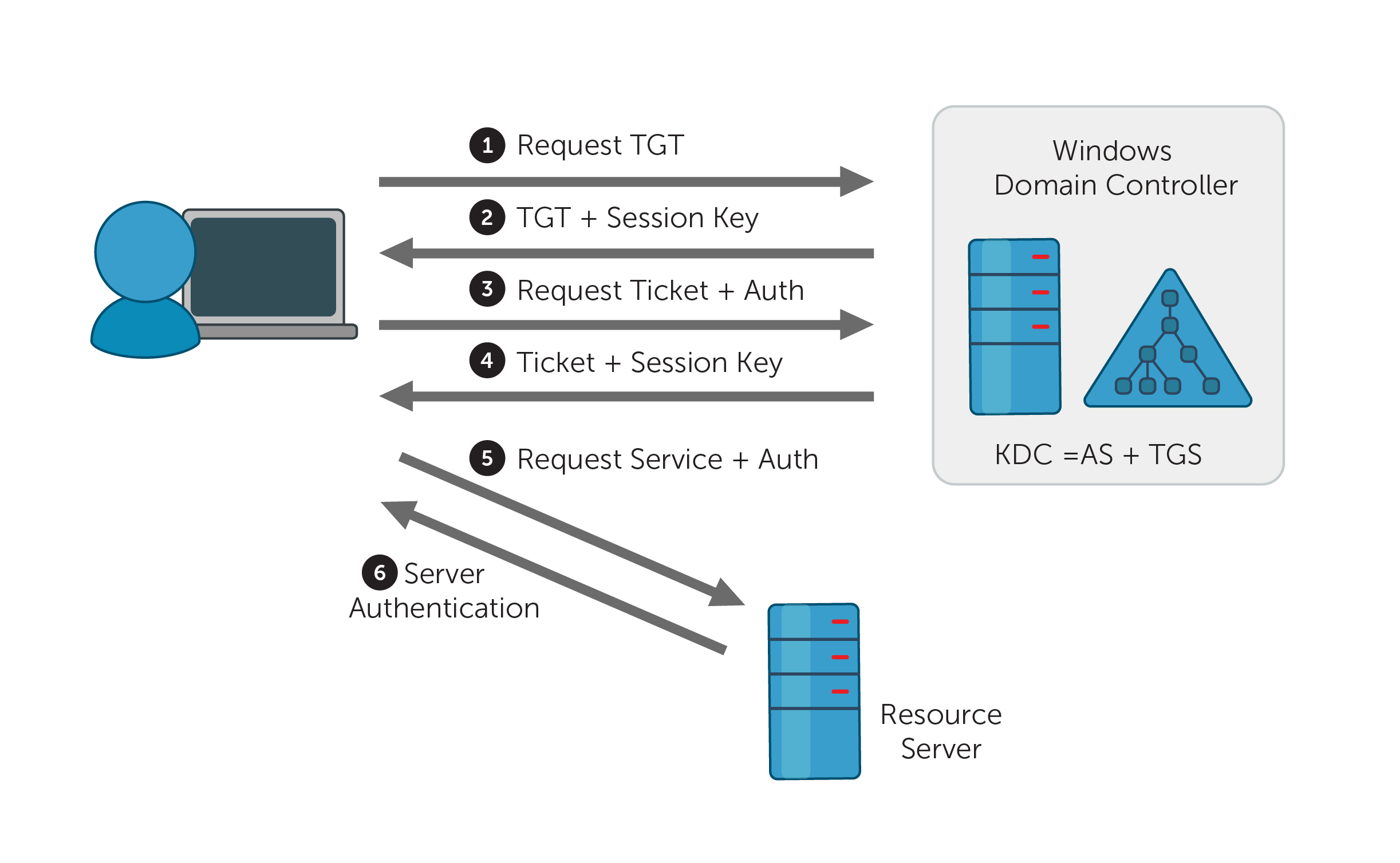
Authentication package Windows Kerberos is the standard certification pack in Windows Server 2004, Windows Server 2008 and up to Windows Vista. It coexists with the NTLM Challenge / Response protocol and is used in cases where both client and server can negotiate Kerberos. Request for Comments (RFC) 1510 specifying that the client should send the User Datagram Protocol (UDP) datagram in field 88 to the IP address associated with the Key Distribution Center (KDC) if you are a client using the Contact KDC. The KDC must respond to the send with an rsvp datagram when registering the sender’s IP address. The RFC also states that UDP should be the first protocol to try.
Throttling UDP Packet Machine may cause the following error message when joining the domain:
Event log error 5719
Source NETLOGON
A Windows NT or Windows 3000 domain controller is not available for the Domain sector. The following error occurred:
It looks like there are currently no connection servers available to request a connection.
Error signal 1
Checking the DC list. … … ! … ! … … … … … … … … … Error: [PR WARNING] DsBind cannot be reached at
COMPUTERNAMEDC.domain.com(159.140.176.32). [ERROR_DOMAIN_CONTROLLER_NOT_FOUND]Kerberos preauthentication failed. “This error is more likely in UNIX interop scenarios. MIT Kerberos clients do not request preauthentication when sending the KRB_AS_REQ message. Preauthentication is required (default), Windows brands will send this error.
Error word 2
Kerberos test. … … … … … … … … … ! ! ! ! … : [FATAL] Kerberos failure never has a ticket for MEMBERSERVER $.]The Windows XP event logs: SPNegotiate 40960 and Kerberos 10 demonstrate this issue.
Additional Information
If you are using UDP for Kerberos, your client computing device may stop responding (hang) when someone receives the following message:Upload your DIY settings.
By default, the maximum size of datagram packets for which Windows Server 2003 uses UDP is 1465 bytes. For Windows XP and for Windows This 2000 the maximum is 2000 bytes. A transmission control protocol (tcp) is generated for every datagram packet that exceeds this maximum size. The maximum length and width of datagram packets that use UDP can be set by changing the registry key to the best value and.
. to be changed
Kerberos is primarily a UDP protocol, although it uses TCP for large Kerberos tickets. This may require special firewall configuration to allow UDP responses to the Kerberos Server (KDC). Kerberos buyers must send UDP and TCP packets on port 88 and receive responses from Kerberos servers.
Uses UDP datagram packets by default without connecting to Kerberos. Depending on various safety factors, includingGiven the tradition of identity (SID) and group membership, some accounts may have a larger form of Kerberos authentication package. Depending on the hardware configuration of the virtual private system (VPN), these large packets must be fragmented as they travel through the VPN. The issue is with the fragmentation of these large UDP Kerberos packets. Because UDP is still a connectionless protocol, fragmented UDP blocks are rejected if they can reach their destination in the order in which they were found.
If you do change the MaxPacketSize to 1, you force the client to use TCP to send Kerberos traffic over the VPN tunnel. Since it is TCP connection oriented, it is undoubtedly a more reliable means of transport over a VPN tunnel. Even if the packets were dropped, the web server again requests the absence of the special features packet.
You can change MaxPacketSize to 1 and force clients to use Kerberos over TCP traffic. To do this, follow these registration steps:
Start the editor.
Then find and simply click the registry subkey:
HKEY_LOCAL_MACHINE System CurrentControlSet Control Lsa Kerberos Parameters.Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!
- 1. Download and install Fortect
- 2. Open the program and click "Scan"
- 3. Click "Repair" to start the repair process

Note
If a specific parameter key does not exist, it will be generated now.
On the Modify Recipe menu, point to New and then simply click DWORD Value.
Start Registry Editor.Find and click on the laptop or computer subsection: HKEY_LOCAL_MACHINE System CurrentControlSet Control Lsa Kerberos Parameters.On the Edit menu, point to New and in this case click DWORD Value.Enter MaxPacketSize and press Enter.
Enter MaxPacketSize and press the next ENTER key.
Double-click MaxPacketSize, enter 1 in the Actual Value data field, click the Decimal Number option to select it, and then click OK.
Close the registry editor.
The message contains an invalid checksum. Check what types of valid checksums can be specified in krb5.conf, not to mention the kdc.conf files. The network address does not match. The network reward in the ticket prepared for routing was different from the address of the online circle in which the ticket would appear to be processed.
Restart your computer.
This is considered a solution for Windows 2007, XP, Server and 2003. Windows Vista and newer uses 0 more for MaxPacketSize, which also means using UDP to accept Kerberos client.
Below is a web design, administrative template that you can import into Group Policy if you want. Why not set the MaxPacketSize value for all corporate computers that have Windows Server 2003, Windows XP, and Windows 2000 installed? Review the maxpacketsize options in In the Group Policy Object Editor, select Show Policies Only from the View menu so that Show Policies Only is not selected. This structure modifies registry keys outside of the Policies section. By default, Group Policy Object Editor does not display these PC settings.
- Read 4 minutes
RFC 4120 currently supersedes RFC 1510. RFC 4120 means that the KDC should accept TCP requests and should expect the same number of requests on port 88 (decimal). By default, Windows Server 2008 and Windows Vista try TCP with Kerberos first, because the default Maxpacketsize is now definitely 0. You can always implement the MaxPacketSize registry entry to overcome this behavior.
This section, method, or work item contains steps that tell you how to modify the registry. However, serious problems can occur if you modify the registry incorrectly. So make sure you follow these steps carefully. To be on the safe side, back up this registry before modifying it. Then someone can restore the registryp if he has problems. For more information on backing up and restoring the registry, see Backing up and restoring your Windows computer’s Windows registry .
Download this software and fix your PC in minutes.6863 Kerberos Erro De Autenticacao Udp
6863 Errore Di Autenticazione Kerberos Udp
6863 Kerberos Autentiseringsfel Udp
6863 Error De Autenticacion Kerberos Udp
6863 Oshibka Autentifikacii Kerberos Udp
6863 Kerberos Authentifizierungsfehler Udp
6863 Kerberos Authenticatiefout Udp
6863 Blad Uwierzytelniania Kerberos Udp
6863 Kerberos 인증 오류 Udp
6863 Erreur D Authentification Kerberos Udp