An Easy Way To Fix The Creation Of Checksum Files
December 28, 2021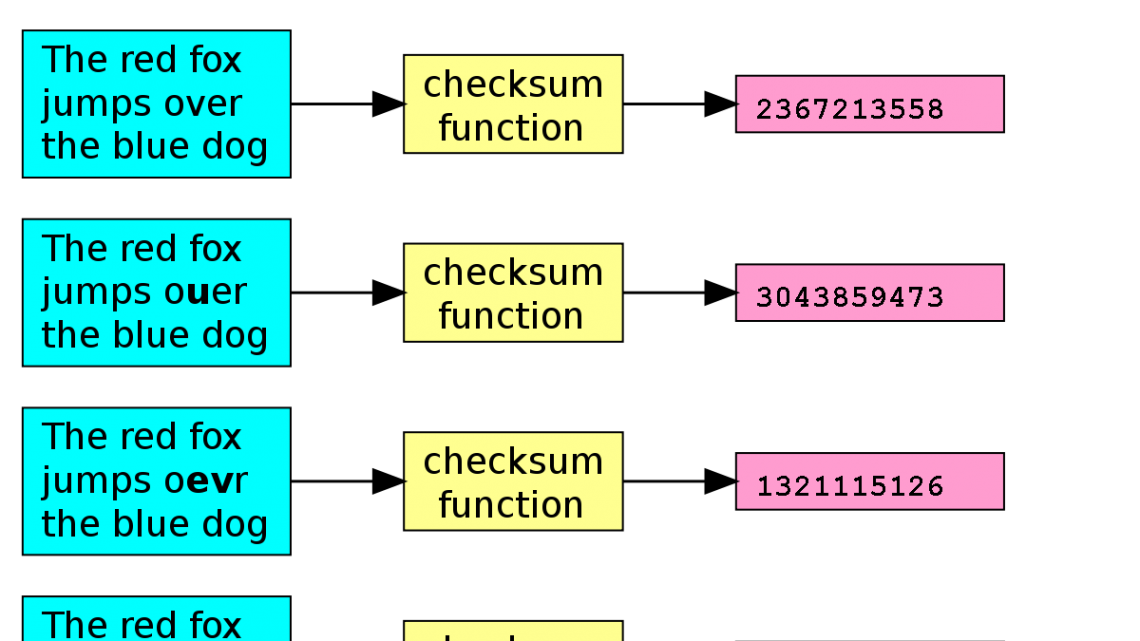
Recommended: Fortect
Here are some simple steps that can help you solve the problem of creating a checksum file. g.The checksum is most likely the result of running an algorithm formula called a cryptographic hash function found for a piece of data, usually your separate file. By comparing the checksum that most of you generate from your version referencing the file with the checksum reported by the originator, you will ensure that your copy of the file is genuine and error-free.
A checksum is the result of executing an algorithm called a critical cryptographic hash function on a piece of data, usually in a single file. Comparing the checksum you generate directly from your version of the file provided by the file’s lender helps ensure that your copy of the file must be genuine and free of errors.
This article describes how to generate MD5 and simple SHA checksums and check the integrity of files in Linux.
What is a checksum?
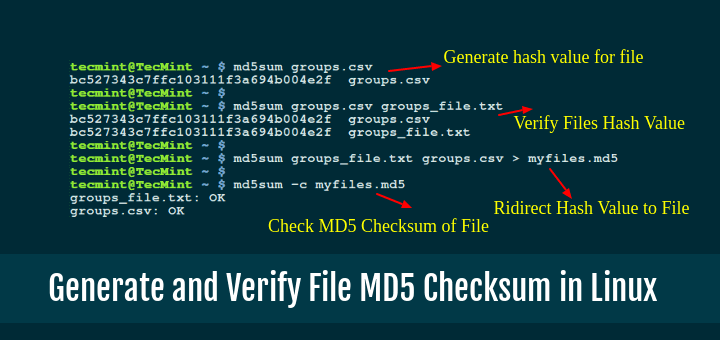
Enter the following command: md5sum [enter file name and format here] [file path] – NOTE. You can usually drag the file into the Terminal window instead of entering the full path. Press the Enter key. You will see the total MD5 of the file. Compare it with the original value.
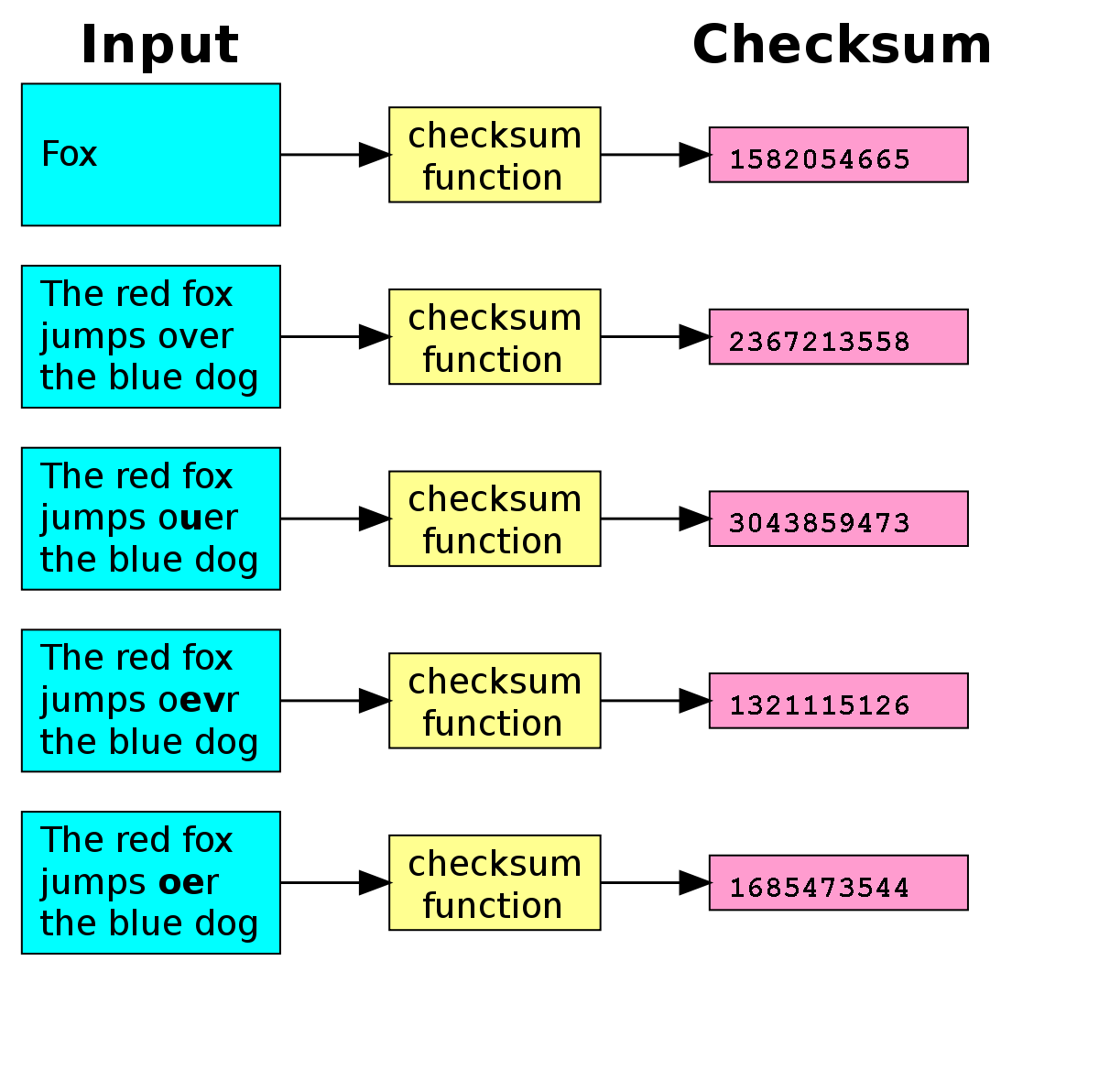
A checksum (sometimes called a hash) is an alphanumeric content value that uniquely represents the content using a file. Checksums are widely used to verify the integrity of computer data files downloaded from an external source such as an installation file. You should also be able to use checksums to verify the integrity of your own files. For example, you can generate checksums based on backup files and then use checksum algorithms or a hash tool to make sure they don’t get corrupted or changed later. If the two checksums match, the files are the same.
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!

The two most common checksum rules are MD5 and SHA. If the checksums are correct, you need to make sure that someone is using the same algorithm aswas probably used to generate the checksum. For example, the checksum of an MD5 file is completely different from its SHA-256 checksum value.
Generating checksums in Linux
All A2 servers run Linux and therefore process command line programs to generate MD5 and SHA checksums.
To generate a save checksum and save the value in a new file, do the following:
- Log in to your account on the marketplace using SSH.
- Enter one of the commands after when ordering and replace the file name with the file ID customers want to create a checksum for:
- To return the MD5 checksum, enter:
To generate an MD5 checksum, enter: md5sum filename> md5sums.txt.To enter the SHA checksum, enter the command status, usually for the hashing algorithm you want to useuse.
md5sum filename> md5sums.txt
To generate the SHA checksum, enter the command for the specific hashing algorithm you want to start with. For example, to generate a checksum, use the sha-256 sha256sum command. To generate a SHA-512 checksum, enter the following command:
sha512sum filename> sha512sums.txt
The md5sums.txt (or sha512sums.txt) Lodge now includes a file and directory site with matching checksums.
You can also receive multiple checksums at the same time. For example, to generate MD5 checksums for all files most commonly associated with .zip files in the current directory, enter the following command:
amount md5 * .zip> amount md5.txt
To generate MD5 checksums for all videos in the current directory and each of the directories below, immediately enter the following command:
find
. -type f -exec md5sum> md5sums.txt ; To get SHA checksums instead, replace md5sum with the appropriate sha command.
- To return the MD5 checksum, enter:
Check checksums on Linux
All A2 hosting servers run Linux, so command line tools are used to validate MD5 and SHA checksums.
- Log in to your SSH account.
- When prompted for influence, enter one of the commands based on the Ou algorithm used (md5 SHA) and generating checksums. They use the file names md5sums.txt and sha512sums.txt. If the checksums of the storage familyThey are stored in a special file, this filename is used instead.
- Enter md5 to verify checksums:
md5sum -c md5sums.txt
To evaluate SHA checksums, enter the specific command name for the clients of the hash algorithm to be used. For example, to check the SHA-256 checksum, use my sha256sum command. To verify the sha-512 checksum, enter the required command:
Open the Windows handle line. Do it quickly: Press Windows R, type cmd and journal and press Enter.Go to the directory containing the file for which you want to verify the MD5 checksum and perform additional verification. Command: Enter cd and specify the path to the folder.Enter certutil -hashfile
MD5!Hit Enter. sha512sum -c sha512sums.txt
Open any Windows command prompt. Hurry up: press Windows R, type cmd and press Enter. ! !Go to the folder containing your current file you need to check and check the MD5 checksum.Enter certutil -hashfile
MD5.Hit Enter.Compare the received checksum to see what to expect. Any checksum match though indicates OK, the platform checksum doesn’t match the error.
If you check for an incompatible file property, the results of any of the scrolling results may be lost. To display only mismatched checksums, consider the silent option. For example:
sha512sum --quiet -c sha512sums.txt
- Enter md5 to verify checksums:
Other operating systems
- For a specific Microsoft Windows machine, you should definitely install one of the many downloadable software packages that generate and validate benchmarks.the amount.
- Can md5 be used with Shasum’s have products on an Apple macOS computer?
Additional information
- For more information on the MD5 hashing algorithm see https://en.wikipedia.org/wiki/MD5.
- For more information on the SHA family in hashing algorithms see https://en.wikipedia.org/wiki/Secure_Hash_Algorithms.
“SHA” is a general term for a whole family of hashing algorithms. The two most commonly used algorithms are:
- SHA-1
- SHA-2: This colony contains several hash functions whose readers determine the bit length of the hash value (for example, SHA-224, SHA-256, SHA-384, and SHA-512). May
You can also create multiple checksums once. For example, to generate MD5 checksums for all .zip files in the current directory, use the following command:
amount md5 * .zip> amount md5.txt
To generate MD5 checksums to get all files in the current directory and all directories in it, enter the following command:
find
To generate test cases instead We are SHA, replace the corresponding SHA command with md5sum.
If you are examining a large number of files, mismatched results may be lost when scrolling through the results. To display only mismatched checksums, use the silent option. For example –quiet:
sha512sum -c sha512sums.txt
To generate its checksum, you run the program that Raya runs this file using an algorithm. Typical algorithms used for this are MD5, SHA-1, SHA-256, and SHA-512. These methods use a cryptographic hash function that takes input and generates a large, fixed-length alphanumeric string regardless of file size.
“Two files can have the same md5 hash only if their contents are exactly the same; even one option would result in them simply having completely different hash values. ” – It is not right.
Geracao De Arquivo De Checksum
Prufsummendateigenerierung
Generacion De Archivo De Suma De Comprobacion
Generering Av Checksummafiler
체크섬 파일 생성
Checksum Bestand Genereren
Generazione Di File Di Checksum
Generaciya Fajla Kontrolnoj Summy
Generation De Fichier De Somme De Controle
Generowanie Pliku Z Suma Kontrolna