Solved: How To Recover Event ID 5157 Log 6
December 2, 2021
Here are some simple techniques that can help you troubleshoot Event ID 5157 in Log 6.
Recommended: Fortect
Type of. Bug audit. Windows Wood logs event 5157 when WFP drops the connection between the program and the process. This different process can now reside on the same computer in addition to the remote computer.
This event occurs when when Windows Filtering Platform closes the connection.
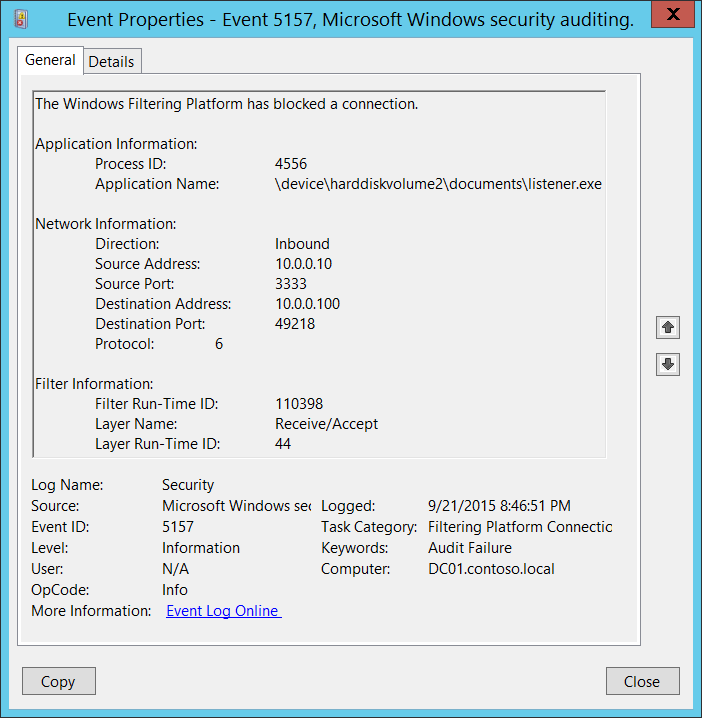
Note. Recommendations for this event can be found under Security under Monitoring Recommendations .
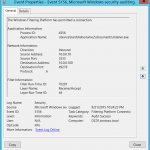
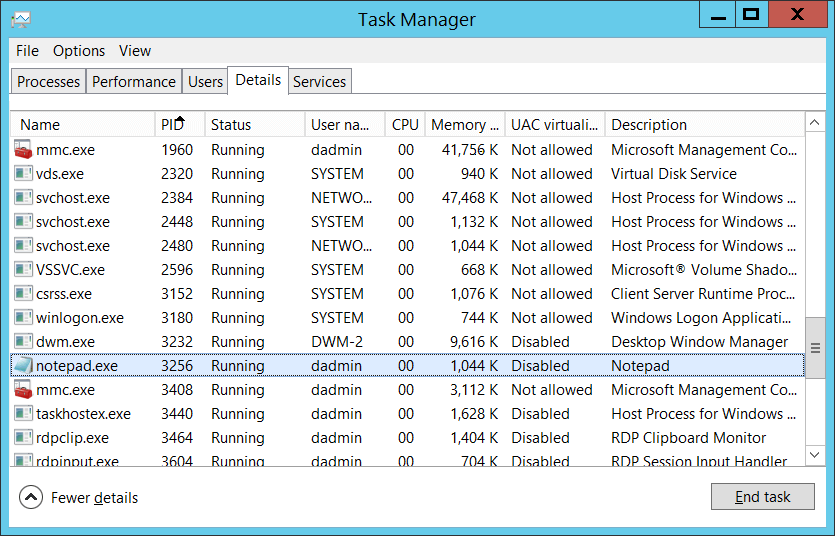
- - 5157 1 0 12810 0 0x80100000000000000 304390 Security DC01.contoso.local - 4556 device harddiskvolume2 documents listener.exe %% 14592 Name = "SourceAddress"> 10 3333 10.0.0.100 49218 6 110398 %% 14610 44 S-1-0-0 S-1-0-0 Process ID [type = pointer]: hex The addecimal identifier of the process that tried to establish the connection. The Process ID (PID) is a number used by these operating systems to uniquely identify each active process. To display the PID of a specific process, you can, for example, use Task (Supervisor Details tab, PID column):
If you convert the type from hex to decimal, you can compare it with the values in Task Manager.
You can now map this process ID to the process ID in other events, for example “ 4688 : New Process Created” Process Info New Process ID.
Application name [UnicodeString type]: = full path and I would say the name of the executable file for each process.
Logical is the hard drive that appears in the hard disk device harddiskvolume # folder. You can get the volume of all rooms using the Diskpart power supply. Command for accessing volume numbers using Diskpart – “Volume List”:
Direction [Type is UnicodeString]: The direction of the connected connection.
Inbound – for incoming connectionsniy.
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!
- 1. Download and install Fortect
- 2. Open the program and click "Scan"
- 3. Click "Repair" to start the repair process

Outbound – for unrelated connections.
Source Address [Type = UnicodeString]: the local IP address through which the iPhone application received a connection.
The Packet Drop Audit Filtering Framework determines whether a statement generates audit events when packets are typically dropped by the Windows Filtering Framework. A large number of reduced packets may indicate that an attempt was made to establish unauthorized connections to computers on your network.
IPv4 Address
IPv6 Address
:: All – IPv6 IP addresses
0.0.0.0 – all IP-addresses in the format
127 ipv4.0.0.1, – :: 1 local
Source Port [Type = UnicodeString]: The port number from which the application received a connection.
Destination Address [Type = UnicodeString]: The IP address potentially initiated by the received connection.
IPv4 Address
IPv6 Address
:: All – IPv6 IP Chat
0.0.0.0 – all IP-addresses in the format
127 ipv4.0.0.1, :: 2 – local
Destination Port [Type = UnicodeString]: The port that was used by the remote computer to initiate the connection.
Protocol [type assumes UInt32]: number of the standard protocol used.
| Service | Protocol number |
|---|---|
| Internet Control Message Protocol (ICMP) | 1 |
| Transmission Control Protocol (TCP) | 6 |
| User Datagram Protocol (UDP) | 17 |
| Generic Routing Encapsulation (PPTP data over GRE) | 47 |
| IPSec Authentication Header (AH) | 51 |
| IPSec Encapsulation Security Payload | 50 |
| External Gateway Protocol (specifically) (EGP) | 8 |
| Gateway Protocol (GGP) | 3 |
| Host Monitoring Protocol (HMP) | 20 |
| Internet Group Management Protocol (IGMP) | 88 |
| With Remote Virtual Disk (RVD) | 66 |
| OSPF Open Shortest Path First | 89 |
| Packet Protocol Universal PARC (PUP) | 12 |
| Reliable Datagram Protocol (RDP) | 27 |
| QoS Redundancy Protocol (RSVP) | 46 |
Filter Runtime ID [Type = UInt64]: Unique ID of the filter that blocked the connection.
To find a specific filter ID trusted by the Windows Filtering Platform, run the following command: netsh wfp show filter. As a result of this command, the image filter.xml is generated. Open this content and find a specific substring with the resulting filter identifier (
), for example: Layer name [Type = UnicodeString]: Application Application The name of the cover layer. Runtime
Monitoring Windows Home Monitoring is a Windows property that helps maintain security in computer and administrative networks. Windows Monitoring is used for tracking user activity, forensic and incident investigations, and troubleshooting.
Layer ID [type is UInt64]: The ID of the Windows Filtering Platform corpus. To find a specific Windows Filtering Platform Level ID, run the following command: netsh wfp show state. The user’s wfpstate.xml file is created as a new result of this command. Open this file and find the qualified substring with the required layer id (
), for example:
Security Best Practices
If you have a large out-of-the-box application that needs to be purchased to perform the operation that is primarily signaled by this event, look out for App checks, which is not a custom application.
You can keep track of whether “Application” is in the default folder (for example, in Internet files). You
If you do have a predefined list of restricted podsstrings, perhaps words in application names (for illustration “mimikatz” or “cain.exe”), check it with substrings in … “Application”
Make sure the “source address” is one of the addresses assigned to the computer.
If a computer component cannot access the Internet, or only contains situations that do not connect to the Internet, watch for events 5157 , where “Target Address” is the IP address on the Internet (not from private IP ranges).
If you know that your office computer should never, under any circumstances, be associated with specific IP addresses on the network, look for those addresses in the Destination Address field.
If you have a list of IP addresses that most computers or devices need to communicate with or simply communicate with, track all IP addresses using a “destination address” that is not on the primary authorization list.
If you need to keep all incoming connections on a special local port, monitor 5157 conferences with this “source port”.
Keep track of everythingand connections using a “protocol number” not typical for this computer or computer, for example, greater than 1, 6, or 17.
If a specific “destination port” is always used to communicate between the primary computer and the “destination address”, monitor all other “destination ports”.
- 4 minutes to read.
Identifikator Sobytiya 5157 Protokol 6
Id De Evento 5157 Protocolo 6
Ereignis Id 5157 Protokoll 6
Identifiant D Evenement 5157 Protocole 6
Handelse Id 5157 Protokoll 6
Identyfikator Zdarzenia 5157 Protokol 6
Id Evento 5157 Protocollo 6
Gebeurtenis Id 5157 Protocol 6
Id De Evento 5157 Protocolo 6
이벤트 Id 5157 프로토콜 6