How To Fix Wep Key Cracking Issues In Windows XP?
January 21, 2022
If you’ve noticed the Wep key hack in Windows XP, this guide should help you.
Recommended: Fortect
Standard 64-bit WEP uses almost any 40-bit key (also known as WEP-40) combined with a large 24-bit initialization vector (IV) to represent the RC4 key. Second, that the original WEP standard must have been developed, limited the serious scope of the US government’s directives on the export of cryptographic technology.
Chris, so you can write: Not to mention, cracking WEP is a waste of time. Cracking a properly generated WEP key (in other words, this WEPAtack or other dictionary-based Christmas crackers won’t work) takes a long time because it’s counterproductive. Ask others. Apart from people who have often cracked their own WEP, very few have successfully cracked the male or female WEP button. It takes too long and there are other, easier ways to attack the network. We have discussed this several times in the Key Facts forum, so I am not going to go into detail here. However, if you do a regular penetration test (read: not just all WiFi), it makes sense to attack something other than WiFi first. You will find your success much higher and faster.
I want all the dosgifts. You don’t seem to understand what you are talking about.
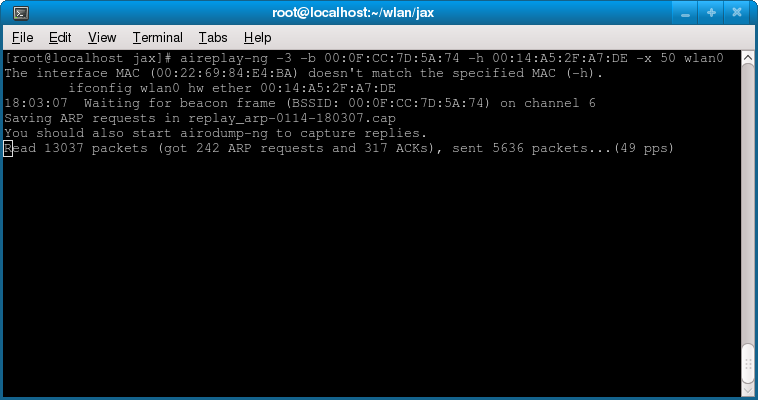
With enough packets, 64 or 128 keys can be cracked in less than 30 seconds. It is also possible to implement statistical methods to crack the factor, even corrected with firmware cards. And it is also possible to generate data traffic over Wi-Fi (without mastering the key) to collect enough boxes to launch a successful statistical attack and recover the key.
And almost all businesses have their own Wi-Fi connected directly to their local network, so if we can crack WEP, you and your family will bypass your vital security perimeter (firewall). Sometimes (depending on which mode the access point is configured in), it is possible to initiate advanced Arp-Poisson-based sniffing from WiFi in order to save traffic on the internal LAN, password sniffing, defect hijacking, identity theft and, of course, the ability to access a multitude of servers and services that are, of course, only accessible from the inside.
If you still think that really few people have cracked WEP encryption However, you should look for most good tools for this.
And, after all, talking about security is legal. We’re not talking about intruding into someone else’s network, but rather secure WEP encryption algorithms that make networks wireless. But … perhaps, as the Matrix said … “en ignorancia la encuentra la felicidad” …
Cracking WEP is usually pretty straightforward.Understand if families followed the explanations in this article. we are runningI was struck by the And iv WEP encryption and how they are connected. PutIt’s amazingly simple: if you can decipher every iv algorithm, you can decipher moreremove the WEP key.
As I mentioned earlier, WEP sends very well Clear a specific IV, so if many of us can map a math system to a system, then we can find and compute the rc4 stream that encrypted the type of the whole packet into the one at the beginning.
Access the main router configuration list.Click on the top menu.Press.In the Select a WEP Key section (step 5 in the Basic Security Settings section), enter the new key system in the Key Code field.Scroll to the bottom of the sheet to help you, then click.
There is no price tag in the WEP “key” [key]it’s a mathematical equation. Do you remember which access point or client has this key?Used in cases where, when decrypting a packet, most people need tobe it somehowcomplex algorithm against encrypted packet.
WEP is a snooping encryption based on never using the same tee.n key twice to ensure security. Keep in mind that cyberpunks cannot even grab a handshake like an empty WPA network, but even fantastic empty WEP networks can be attacked with packet injection.
If everyone thinks of it this way, the concept might become clearer:
you there is a protocol that is generated by randomly linking each of them24-bit IV generated by your WEP key – you also have RC4 key for streaming on the internet – both are then hashed at the same time to encrypt the packet.
IV is in fact the basis of the entire procedure, because it is the only thing that needs to be doneYou have used your WEP key. If we do an accurate IV analysis forThen try to decrypt the packet, we can get the key that was used at the beginning of one ofprocess.
If you try to decipher it every time you receive Part of the algorithm, I would say the corresponding part of the plaintext of your packageis expanded after decrypting the packet, you know you are programming the programused to encrypt this very packet – a rough way of describing itbut as simple as possible.
Any attacker can be passive.collect encrypted data, but after thatdue to discussed limitationspreviously; collected two identical IVs. Packages with two waterfallswith the same IV almost always XOR, XOR of standard text data can bedisclosed. This XOR can then be used to get the interior data.data packages. The more
identical IVs collected, the moreResults may be displayed in plain text. Once all the plaintext of the data is thisThe package is known, it is also known primarily for all data packages by addingthe same IV.
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!

Thus, before any broadcast, WEP concatenateskeystream, working with the payload using the XOR action plane,Encrypted text (data encrypted again). WEP contains a clear IVthe first contains a small number of frame bytes. Endpoint / client uses this Shared Secret IV (your WEP key) to decrypt the exactFrame payload.
Download this software and fix your PC in minutes.WEP uses the RC4 algorithm to encrypt information packets sent from an access point or wireless LAN device card. Once the access state receives the sent packets, the user’s NIC decrypts each one. Each byte of data remains encrypted with a different packet ratio.
Hacka Wep Nyckel I Windows Xp
Hackear Clave Wep En Windows Xp
Vzlomat Klyuch Wep V Windows Xp
Wep Sleutel Hacken In Windows Xp
Hackear Chave Wep No Windows Xp
Windows Xp에서 웹 키 해킹
Wep Key In Windows Xp Hacken
Hackerare La Chiave Wep In Windows Xp
Pirater La Cle Wep Sous Windows Xp
Hackowanie Klucza Wep W Systemie Windows Xp