How To Fix Sound Activation In Windows 7
February 9, 2022
Recommended: Fortect
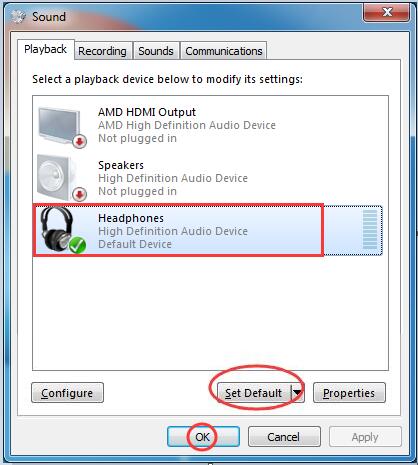
Today’s guide is written to help you when you receive the “How to turn on sound on Windows 7” error message. Open the control panel.Click Hardware and Sound, then click Sounds.On the Playback tab, click directly in the blank area and make sure there is a check mark next to Show Disabled Devices. If headphones / speakers are disabled, they will appear in the list.Right click the device and activate it.
Win32:Trojan-gen is a heuristic for detecting generic Trojan horses. Due to the general characteristics of this threat, we are unable to provide specific information on its impact. Send information in the region of your PC, including usernames and browsing history, to a remote malicious zero.
What is Win32: Trojan horse genome infection?
Method 1: Update Personal Audio Device Drivers AutomaticallyMethod two: manually uninstall and reinstall the device driver.Method or better: reactivate the device.
In this short article, you will find the basic interpretation of Win32:Trojan-gen, as well as its negative impact on your technologies. This ransomware is typed malware used by online scammers to ask the victim to pay a ransom.
In most cases, a Win32:Trojan-gen infection will directly tell its targets to initiate a cash flow to counter the changes that the infected Trojan has actually made to the target of the toy car.
Win32 Trojan Summary
- Extract executable code. Cybercriminals repeatedly use binary packers to prevent your malicious code from being reverse engineered by spyware and adware analysts. The Packer is a job site maintenance tool that compresses, encrypts, and re-formats malicious files. Sometimes packers can also be used for legitimate purposes, such as protecting a program from hacking or.
- Injection (Inter-Process);
- Injection (Process Hollowing);
- Creates pacrush RWX. There is a memory area security trick that allows an attacker to fill the barrier with shellcode and then execute it. Buffer fullness as the cause of the shellcode doesn’t matter, it’s mostly data. The problem arises when an attacker can take instruction control (EIP), a pointer that is typically written by corrupting the stack frame of a function with a better stack-based buffer overflow, and then increase execution throughput with that pointer. address with shellcode.
- Get data related to own binary image. A trick that allows malware to extract data from your computer’s memory.
Everything you do, type or click on your computer goes through memory. This includes passwords, bank account numbers, email addresses, and other sensitive information. Is it possible that this vulnerability could be used by malware to extract this data?
- The likely binary contains password-protected or compressed data. In this statement, encryption isvirus code tracker from anti-virus programs and therefore anti-virus scanners.
- Starting a process and its style when it was probably unzipped;
- Collecting records. about installed applications;
- Creates a hidden system file. The malware adds its hidden attribute to every file and folder on your system, so anything recently deleted from your hard drive will be visible.
- Activity detected by the network, but not in the API logs. Microsoft has integrated an API solution directly into the Windows operating system that displays the network activity of almost all applications and programs running on a computer in the last 30 days. This masks malicious network activity.
- Produces text a from itself;
- Anomalous binary strokes. This is a way to confuse the code of viruses and virus analysts.
- Encrypt your documents on the target drive so that the living can no longer use the data;
- Prevent routine access to the worker’s workplace. This is the typical behavior of a virus called Locker. It blocks access to the computer untilUntil every one of our victims pays the ransom.
Similar behavior
Related domains
Win32: Trojan Horse Gene
On your keyboard, press the Windows Layout key and R at the same time to open the Run dialog box.Sign in to services.Right-click Windows Audio and select Properties.Set the Startup Type to Automatic and click OK.Right-click Windows Audio and choose Restart.
One of the most common networks that bundle Win32:Trojan-gen:
- Via phishing emails;
- Significant impact when a user accesses from a resource that hosts a malicious computer program;
After successfully injecting the Trojan, it encrypts information on most of the target’s computers or prevents the device from working properly – in addition to adding an actual ransom note stating that those concerned want a refund for the target resulting from the global decryption. documents or document system recovery should be traced back to the underlying problem. Perhaps most of the ransom note comes during a quick reboot of the client’s PC, because the system has already been compromised before.
Win32: Trojan distribution channels.
A new world, Win32:Trojan-gen, is growing rapidly in various places. However, ransom methods and notes forI receive my own ransom amount may vary depending on the settings of a specific locale (locale). Ransom notes, as well as representations of the receipt of the ransom amount, may vary depending on (local) topographical conditions.
- 1. Download and install Fortect
- 2. Open the program and click "Scan"
- 3. Click "Repair" to start the repair process
Unlicensed program information error.
Open our own start menu on the desktop and click on Control Panel. Select “Administration” and select “Services” from the menu.Scroll down and double click Windows Audio.Click the Start button to authorize Windows Audio.
In some places, Trojans usually incorrectly report that they have found duplicate applications activated on the technological victim’s computer. The hash then prompts the person to pay the ransom.
Trojan:W32/Agent is actually a subset of the members of the “Agent” family that encapsulates a wide range of malware that does not mix with other known families. The agent family includes trojans, worms, spores, backdoors, and otherdy malware.
False claims of illegal content.
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!

In countries where app piracy is much less common, the method is not as effective due to cyber fraud. Conversely, a Win32: Trojan-gen pop-up warning may falsely claim to be owned by a law enforcement company and will certainly complain that it found child pornography or similar prohibited information on the gadget.
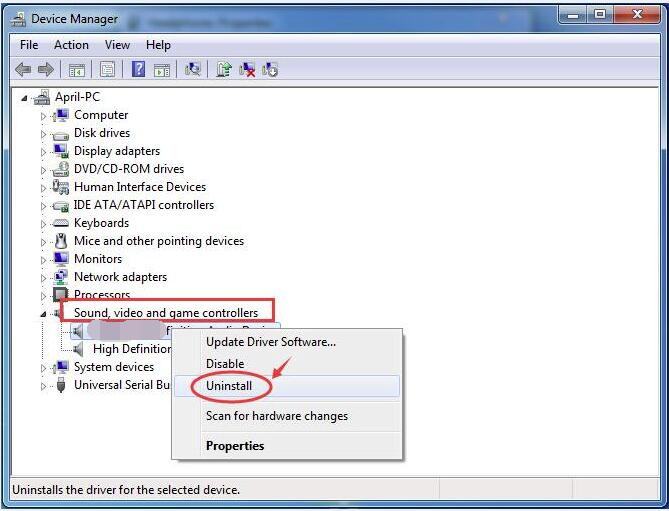
If you don’t hear sound, check Device Manager to select the state of your audio device. Click Start and type Phone Manager in the Start Search workspace. The Device Manager window will open. Right-click the audio device name to select Enableb ”to re-enable the entire device.
Win32:Trojan pop The warning may falsely claim to be sent by a law enforcement agency and will also report the use of child pornography or other content. a excluded from the game data on the device. The warning also includes a demand for payment from the user, often a ransom.
Technical Details
File info:
CRC32: Ad137e5b2ea970fcf1db83d51715f38cname: 8e06ab64md5: 2c.jpgsha1: 78b802f6e90a9bfe7d520cb0ae7fbc7a09b2465csha256: 8309b896b0f7b895e84ac2ad491be11870e20bd101bf8e4b0dc1b8adc85b8530sha512: 5973f43a2af4b9de83339fe44d8269f1e485c7b6b870122116bd17603ebd0919a329607317d28348132094ba9187bb4abeeac5595a8528bfa9b7b8f621f2d724ssdeep: 24576: J7 / k8qDC27Gdi5xx8LvtlWy9BTuC1G86qRkNLhx4UH8A0FdEZbLFNlbfeJV: N / I7UiTx8RlRrlRwhmI8nzUVnGvtype: PE32 ex (GUI) 80386, Intel for MS Windows
Version info:
Legal informationCopyright: xa9IBE Software 2016 All rights reserved.
Download this software and fix your PC in minutes.Trojan. No gene. 2 is a specific generic name for specific malware. It is malicious and poses a huge threat to computer security.
Win64:Malware-gen is a specially designed heuristic detection used by Avast Antivirus because it usually detects a Trojan horse. Win64 Malware gen exe can be an automated ransomware that intercepts and decrypts files on an infected computer and asks men and women to pay to unlock those archives.
So Aktivieren Sie Audio In Windows 7
Jak Wlaczyc Dzwiek W Systemie Windows 7
Hoe Audio In Windows 7 In Te Schakelen
Comment Activer Le Son Dans Windows 7
Como Activar Audio En Windows 7
Como Habilitar Audio No Windows 7
Hur Man Aktiverar Ljud I Windows 7
Kak Vklyuchit Zvuk V Vindovs 7
Come Abilitare L Audio In Windows 7
Windows 7에서 오디오를 활성화하는 방법