Format External Hard Drive From Ntfs To Fat32 Mac Easy Fix Solution
March 5, 2022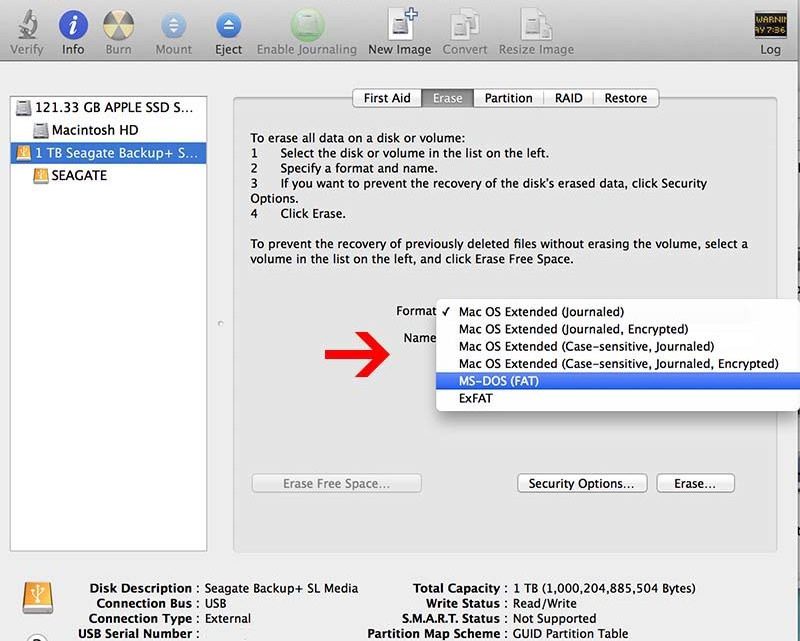
Recommended: Fortect
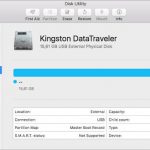
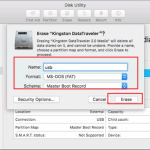
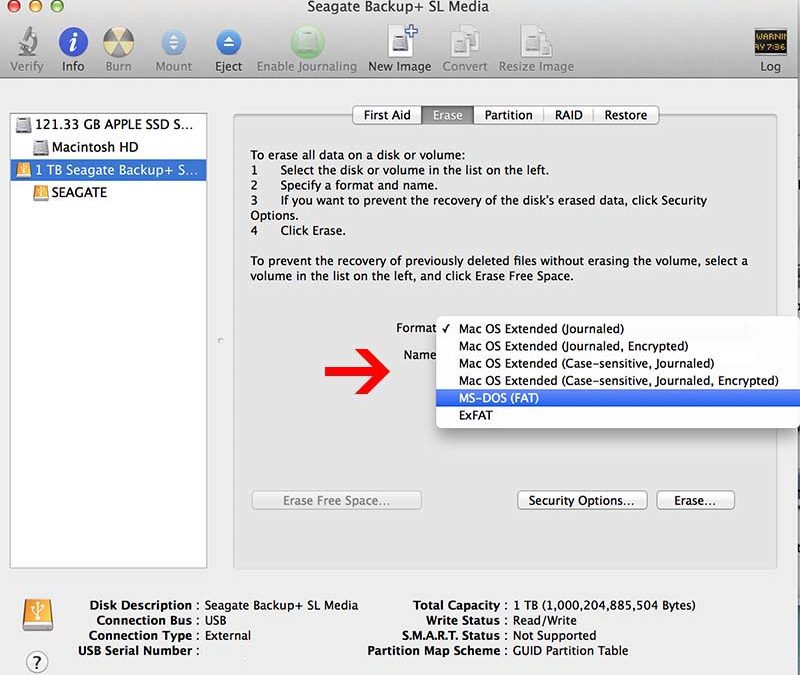
If you want to reformat an external hard drive from NTFS to Fat32 Mac, this article should help you. Insert your USB drive into your Mac. Then buy Applications> Utilities, then launch Disk Utility. Select each USB drive in the sidebar of Disk Utility. From the Disk Utility toolbar, select Erase. Give your floppy disk a name and sometimes choose MS-DOS (FAT32) or ExFat from the Format menu.
PeStudio. >process hackers.Process Monitor (ProcMon)ProcDot.Automatic execution.violinist.Wireshark.x64dbg.
Right click “This PC” or “My Computer” and click “Manage”, activate “Disk Management”.Select your USB drive, right-click it and select Format. Click Yes.Name the drive and select a file system such as “FAT32”. Click OK.You can see that it is FAT32 format.
Learn to flip malware! A popular reverse course that takes an in-depth look at materials and Malware analysis methods. FOR610 training has helped forensic investigators, emergency responders, security engineers and threat analysts gain practical skills in investigating destructive programs that target and attack Windows systems.
Understanding the capabilities of malware is likely to be too important to your ability to receive threat intelligence, respond to cybersecurity reports, and strengthen organizational defenses. This school lays a solid foundation to support malware reverse engineering using a variety of related system and network monitoring utilities, a comprehensive disassembler, a debugger, and many other free tools.
The course starts with the basics of spyware analysis, which will allow you to make decisions beyond the results automatically handled by troubleshooting tools. You’ll learn how to set up a flexible lab right away when you need to understand the inner workings of malware, and how to use the lab to detect xcharacteristics of real malware samples. Also learn how to redirect and intercept traffic at multiple levels in the lab for more information and indicators of compromise. You’ll also begin to learn how to perform compelling code analysis with a debugger.
Recommended: Fortect
Are you tired of your computer running slowly? Is it riddled with viruses and malware? Fear not, my friend, for Fortect is here to save the day! This powerful tool is designed to diagnose and repair all manner of Windows issues, while also boosting performance, optimizing memory, and keeping your PC running like new. So don't wait any longer - download Fortect today!

The course continues with a look at basic assembly language concepts useful for reverse engineering. You will be able to examine malicious code with a disassembler and easily understand decompilers to understand important features other than the flow of execution. In addition, you can learn to identify common malware components by examining suspicious Windows API patterns used by malware.
Start using reverse engineering tools, Ghidra (free), Radare 2 (free), Binary Ninja (paid), IDA Home/Pro (paid) is your preference. IDA is the oldest of these and is still considered the industry standard for static reverse engineering.
Users are then immersed in the analysis of malicious Microsoft Office, RTF, PDF, and Cardstock files, which are frequently used despite being part of a consumer attack chain and being targeted. You will receive guidance on how to learn how to scan for macros and alternative threats that may posethese documents. The course will also teach your organization how to deobfuscate malicious scripts in the form of JavaScript PowerShell and scripts. You will also learn how to examine the shellcode.
Connect the player to your Mac.Open Disk Utility.Select the drive you want to format.Click Remove.Give the drive a descriptive name and keep the default settings: OS X Extended Format and GUID Partition Mapping.Click Erase, but OS X will format those drives too.
Malware is often obfuscated to make scanning difficult, so the guide suggests the ability to unpack malicious Windows executables. You will learn how to flush these types of programs from memory or bypass the packager’s protections using the debugger and advanced technology tools. You’ll also learn practical insights into investigating malware that injects HTML and intercepts APIs by hiding its presence in a diagram or disrupting the flow of information.
The reason MS-DOS (FAT32) is often greyed out on your Mac may still be because this option is not available for the U you are usingSB storage. For example, Mac does not allow families to format SD cards 32GB or less in MS-DOS (FAT32).
For610 virus scanning also teaches you how to deal with malware that tries to protect itself from being scanned. You’ll learn how to detect bypassing common self-protection measures, including no-file special methods, sandbox bypassing, flow misdirection, debugger detection, and other anti-analysis measures.
FAT32 is often used by Microsoft Windows to organize files on hard drives and drives. You can format a good hard drive to FAT32 on a fantastic Apple Mac with Apple’s Disk Utility that comes with macOS. You can also format the disc in a variety of other formats, depending on your needs.
The course ends with a series of “capture the flag” obstacles thatmethods learned in the classroom and allow other companies to learn the practical skills of mining malware in a fun environment.
The most important aspect of this course is hands-on laboratory practice. They allow you to apply malware analysis techniques by examining malware in a controlled and systematic manner. When drawing up training plans, you will study the behavioral models of the samples and examine the percentage of their code. To support your activities, you get ready-to-use Windows and Linux virtual machines with tools for checking and interfacing with malware.
To sum up, the FOR610 malware analysis certification will teach you:
- Create an isolated and controlled lab environment to study malware code and behavior
- Use network and system monitoring tools to study, for example, malware with filesystems, registries, networks, and other processes in Windows environment
- Easily detect and analyze malicious JavaScript code and other website mechanisms thatwhich are commonly used by exploit kits in end-to-end attacks
- Control relevant aspects of software hate behavior by intercepting website visitors and patch code for highly efficient malware analysis.
- Use a disassembler and a good debugger, to study the inner workings of malicious Windows executables.
- Bypassing a set of packers and other defenses designed by malware to deceive r novice authors intercept, confuse and otherwise slow down action, intercept APIs, and take measures against analysis
- Assess the threat associated with vengeful documents such as PDFs and Microsoft Office
< li>Get Indicators of Compromise (IOC) of malicious executables to improve incident response and collect threat intelligence .
The adware and spyware analysis process described in FOR610 rrncident helps responders and other security enthusiasts assess the severity and impact of a malicious computer situation so that theycould plan recovery actions. Forensic experts will also learn about the main characteristics of malware and provide input during an investigation, including how to ultimately identify signs of compromise and capitalize on other threat information to investigate, contain, and contain an incident.
What’s wrong with a malicious or suspicious system? What does its mechanic tell you about the opponent’s goals and abilities? How effective are the company’s home security products against such infections? What measures can strengthen the foundations of the organization from future attacks on this structure? This course provides the skills to answer these and other important questions that are critical to an organization’s ability to deal with malware threats and incidents.
Download this software and fix your PC in minutes.Malware is reverse engineered by disassembling (and sometimes decompiling) a PC program. This process turns binary instructions into mnemonics of code (or much higher level constructs) so that engineers can see what the course is doing and what systems it affects.
You have two approaches to malware scanning: static scanning or active scanning. Static analysis examines the Trojan sample without exploding the object, while dynamic analysis actually runs the adware in a controlled and isolated environment.
Riformattare Il Disco Rigido Esterno Da Ntfs A Fat32 Mac
Formatteer Externe Harde Schijf Van Ntfs Naar Fat32 Mac
Pereformatirovat Vneshnij Zhestkij Disk Iz Ntfs V Fat32 Mac
외장 하드 드라이브를 Ntfs에서 Fat32 Mac으로 재포맷
Reformatar Disco Rigido Externo De Ntfs Para Fat32 Mac
Externe Festplatte Von Ntfs Auf Fat32 Mac Neu Formatieren
Formatera Om Extern Harddisk Fran Ntfs Till Fat32 Mac
Sformatuj Zewnetrzny Dysk Twardy Z Ntfs Na Fat32 Mac
Reformatear Disco Duro Externo De Ntfs A Fat32 Mac
Reformater Le Disque Dur Externe De Ntfs En Fat32 Mac